Secure Boot Setup
sbctl is a user-friendly secure boot key manager capable of setting up secure boot, offering key management capabilities, and keeping track of files that need to be signed in the boot chain.
Installing sbctl
Section titled “Installing sbctl”sudo pacman -S sbctlPre-setup
Section titled “Pre-setup”GRUB Boot Manager
Section titled “GRUB Boot Manager”If you are using GRUB, run the following command to enable secure boot support on GRUB using CA Keys.
sudo grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=cachyos --modules="tpm" --disable-shim-lockEntering Setup Mode in UEFI
Section titled “Entering Setup Mode in UEFI”Firstly, we need to go to firmware settings and set secure boot mode to “Setup Mode”. You can reboot from an already running system to firmware settings with following command.
systemctl reboot --firmware-setup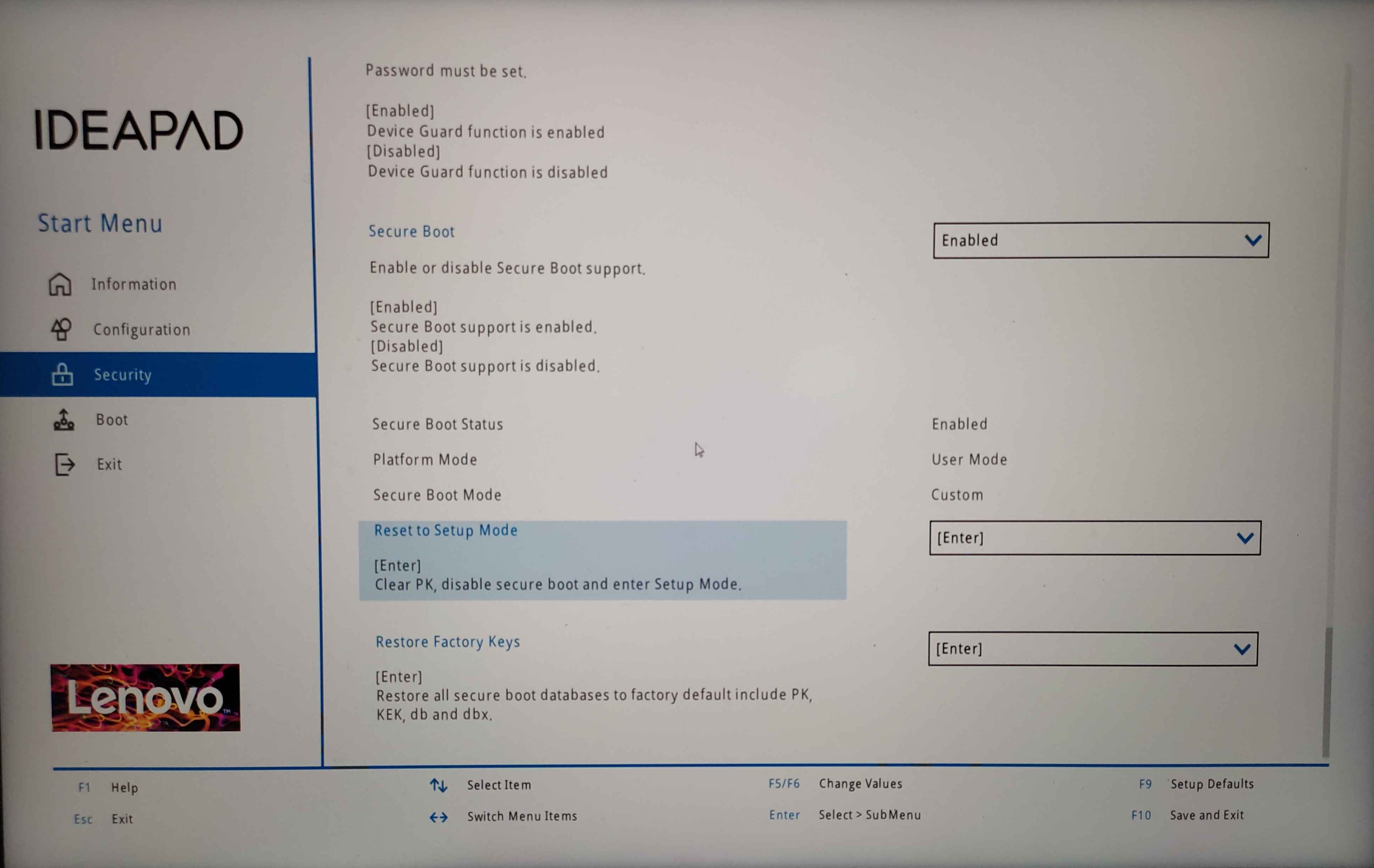
This is how the BIOS looks like on a Lenovo Ideapad 5 Pro. Reset to setup mode or restore factory keys and reboot back to the system.
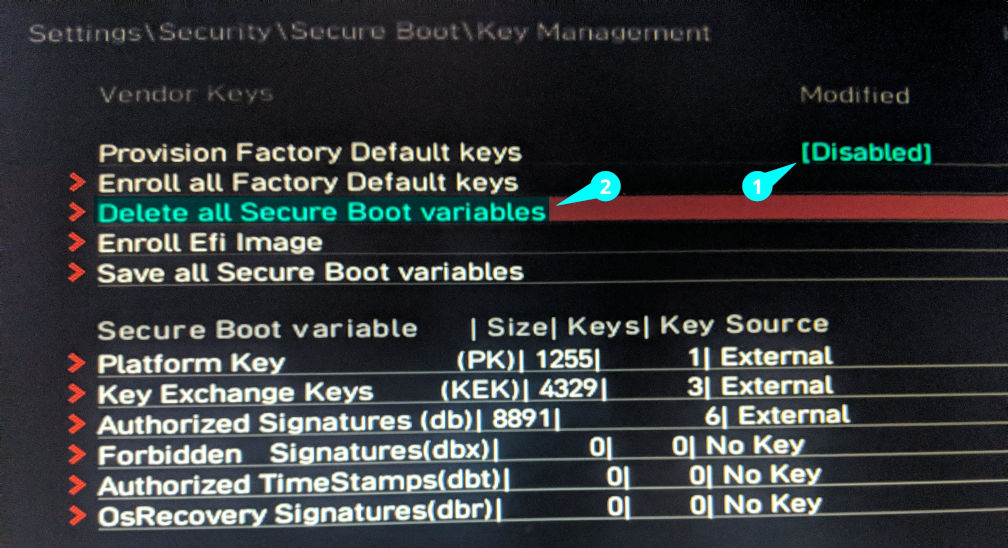
However, some MSI motherboards don’t have a setup mode. To achieve the same effect, follow the two steps from the image below:
Setting Up sbctl
Section titled “Setting Up sbctl”sudo sbctl status # If setup mode is enabled we can proceed to the next stepInstalled: ✘ sbctl is not installedSetup Mode: ✘ EnabledSecure Boot ✘ Disabled
sudo sbctl create-keys # Create your custom secure boot keysCreated Owner UUID a9fbbdb7-a05f-48d5-b63a-08c5df45ee70Creating secure boot keys...✔Secure boot keys created!
sudo sbctl enroll-keys --microsoft # Enroll your keys with Microsoft's keysEnrolling keys to EFI variables...✔Enrolled keys to the EFI variables!
sudo sbctl status# sbctl should now be installed, we can proceed to signing the kernel images and boot managerInstalled: ✔ sbctl is installedOwner GUID: a9fbbdb7-a05f-48d5-b63a-08c5df45ee70Setup Mode: ✔ DisabledSecure Boot ✘ DisabledVendor Keys: microsoftSigning the Kernel Image and Boot Manager
Section titled “Signing the Kernel Image and Boot Manager”CachyOS provides sbctl-batch-sign,
a script that takes the list of files needed to be signed from sudo sbctl verify and signs them all.
Limine users should skip to Limine.
sudo sbctl verifyVerifying file database and EFI images in /boot...✘ /boot/1c4b5246eef05ac3bc87339323cd5101/6.10.0-cn4.0.fc40.x86_64/linux is not signed✘ /boot/EFI/BOOT/BOOTX64.EFI is not signed✘ /boot/EFI/systemd/systemd-bootx64.efi is not signed✘ /boot/1c4b5246eef05ac3bc87339323cd5101/0-rescue/linux is not signed✘ /boot/1c4b5246eef05ac3bc87339323cd5101/6.10.0-cn3.0.fc40.x86_64/linux is not signed
sudo sbctl-batch-sign
sudo sbctl verifyVerifying file database and EFI images in /boot...✔ /boot/1c4b5246eef05ac3bc87339323cd5101/6.10.0-cn4.0.fc40.x86_64/linux is signed✔ /boot/EFI/BOOT/BOOTX64.EFI is signed✔ /boot/EFI/systemd/systemd-bootx64.efi is signed✔ /boot/1c4b5246eef05ac3bc87339323cd5101/0-rescue/linux is signed✔ /boot/1c4b5246eef05ac3bc87339323cd5101/6.10.0-cn3.0.fc40.x86_64/linux is signedNow that all the files are signed, we can reboot back to UEFI settings and enable secure boot.
Note that this is a one-time process as signing files with -s flag will save those files to sbctl’s database.
sbctl ships with a pacman hook meaning it will automatically
sign all new files upon a kernel or boot manager update.
systemd-boot
Section titled “systemd-boot”CachyOS uses systemd-boot-update.service provided by systemd to update the boot manager on reboot. This means that the sbctl
pacman hook will not sign the updated EFI binaries. As a workaround, we can sign the boot manager directly
sudo sbctl sign -s -o /usr/lib/systemd/boot/efi/systemd-bootx64.efi.signed /usr/lib/systemd/boot/efi/systemd-bootx64.efiLimine
Section titled “Limine”Limine is a special boot manager that allows checking the hash of kernel
images and other files that Limine uses during boot. If this is enabled, any
sort of manual configuration done by the user, e.g. signing the image via
sbctl-batch-sign, will modify the hash of the corresponding files and
fail Limine’s checksum verification.
However, signing these files isn’t necessary on Limine because it has a special boot process that bypasses EFI chainloading and signature checks. The only EFI binaries that need to be signed are Limine itself.
# Use limine-enroll-config to sign Limine's EFI binary# This uses sbctl under the hoodsudo limine-enroll-configsudo limine-updateVerify that Secure Boot is Enabled
Section titled “Verify that Secure Boot is Enabled”To check that secure boot is indeed enabled. You can run one of the following commands
sudo sbctl statusInstalled: ✓ sbctl is installedOwner GUID: a9fbbdb7-a05f-48d5-b63a-08c5df45ee70Setup Mode: ✓ DisabledSecure Boot: ✓ EnabledVendor Keys: microsoft
bootctlSystem: Firmware: UEFI 2.80 (INSYDE Corp. 28724.16435) Firmware Arch: x64 Secure Boot: enabled (user) TPM2 Support: yes Measured UKI: no Boot into FW: supportedLinks and Credits
Section titled “Links and Credits”- The Arch Wiki laid the groundwork for this guide. Most of the stuff here was taken from there.
- sbctl - This easy guide to enable secure boot support wouldn’t have been possible if it weren’t for the amazing work done to create this piece of software.
- Improving the Secure Boot Experience by Morten linderud - Blog post by Morten
“Foxboron” Linderud on how the secure boot experience was complicated before
sbctl.